AI-First TPRM™
Fully Integrated Across Our Platform
Leave legacy TPRM behind. Whistic builds AI into every stage of your third-party risk management and customer trust workflows, so buyers and sellers can complete more assessments, generate more insights, create faster business value, and improve security outcomes.

AI brings both sides of the TPRM process together to conduct and respond to more assessments, faster and without cutting corners on security or trust.
High-Impact Insight
Automatically source data-rich responses to control-specific questions using existing security documentation for faster, more meaningful assessments.
Cut Administrative Tasks By 90%
An AI-powered Trust Center centralizes security documentation to increase automation and improve proactive sharing.
Risk Mitigation, Not Spreadsheet Babysitting
AI reallocates valuable InfoSec resources from manual administration to active remediation and true risk management.
Full Transparency
Whistic AI achieves 91% accuracy, but always gives you context with confidence scoring and document citations.
You’re in Control
Audit AI responses for 100% control and visibility, with approved answers increasing the speed and accuracy of future assessments.
The AI Foundation for Modern TPRM
Whistic AI aligns seamlessly with your existing TPRM workflows and capabilities — no add-ons, no widgets. That means it’s part of your processes at every stage, improving your user experience, enhancing your data, and driving deeper insights.
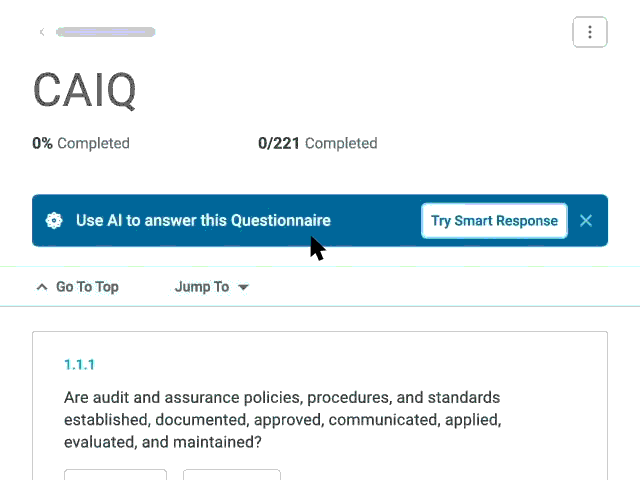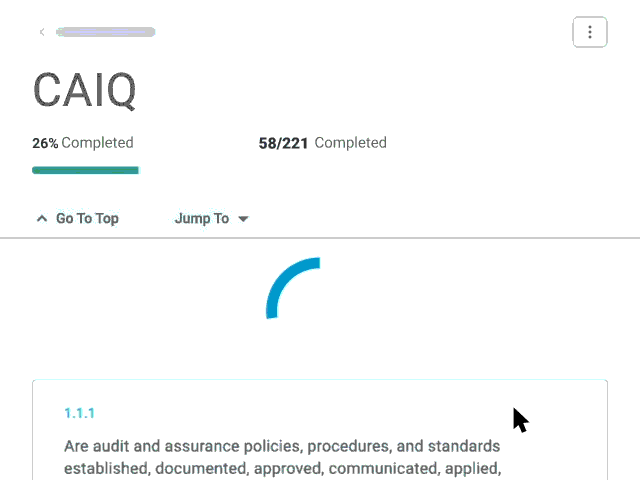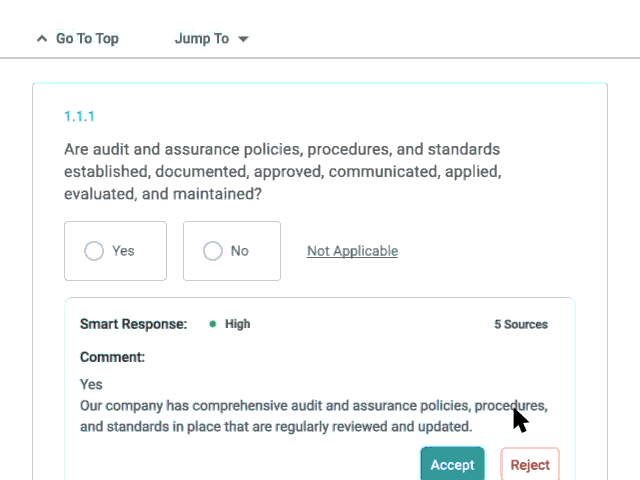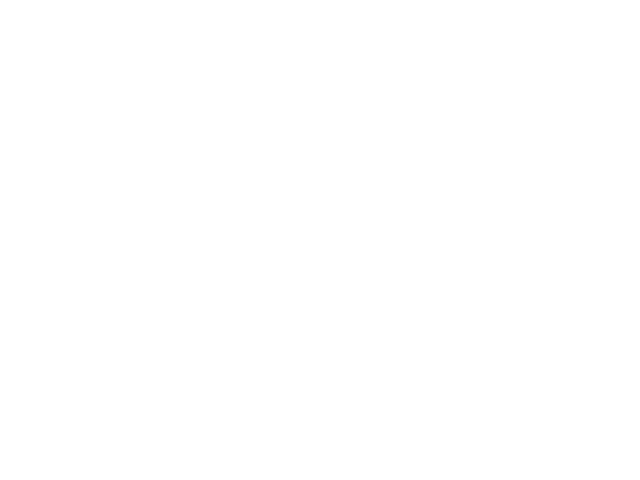
Smart Response
Use Whistic AI to automate the completion of questionnaires (including spreadsheets uploaded into Whistic) by leveraging documents and previously completed questionnaires stored in your Whistic Knowledge Base.
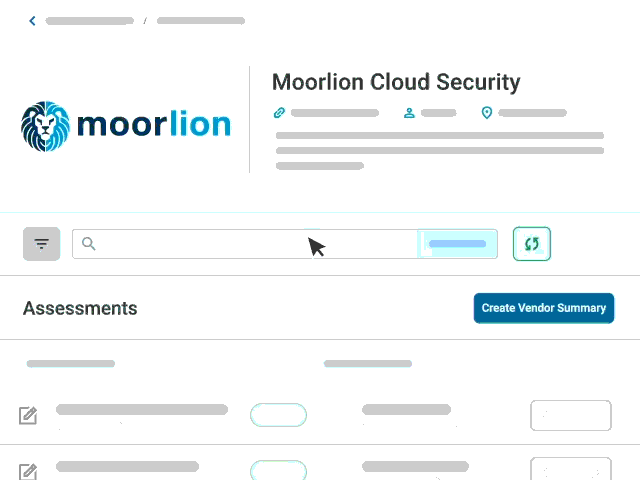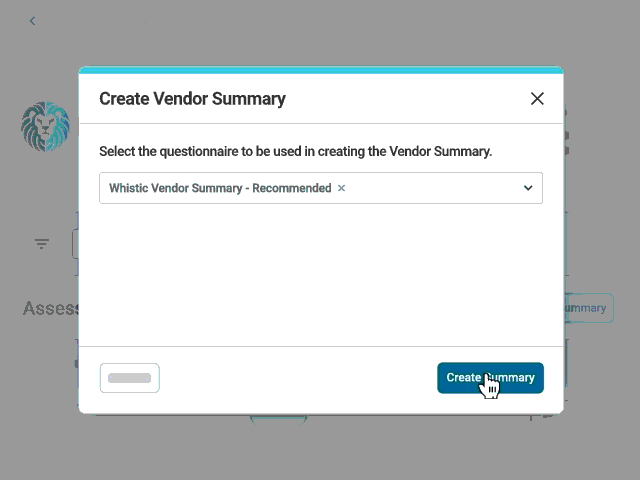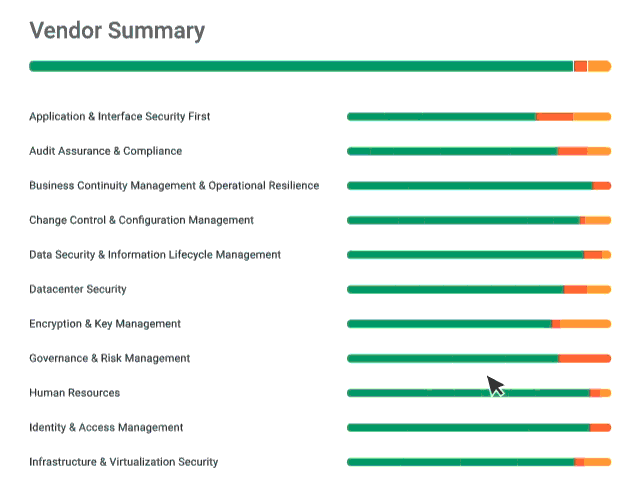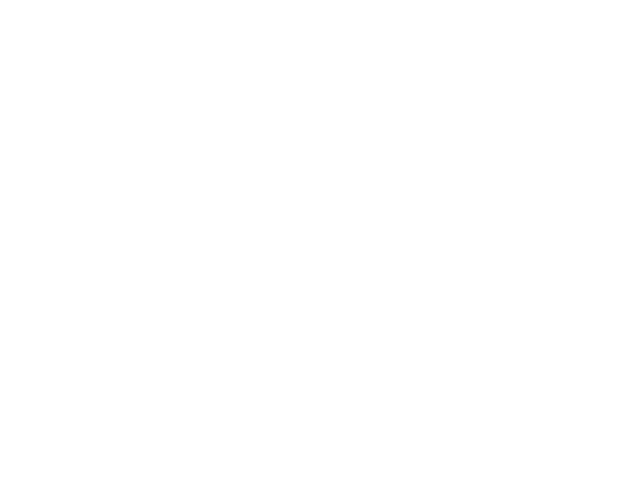
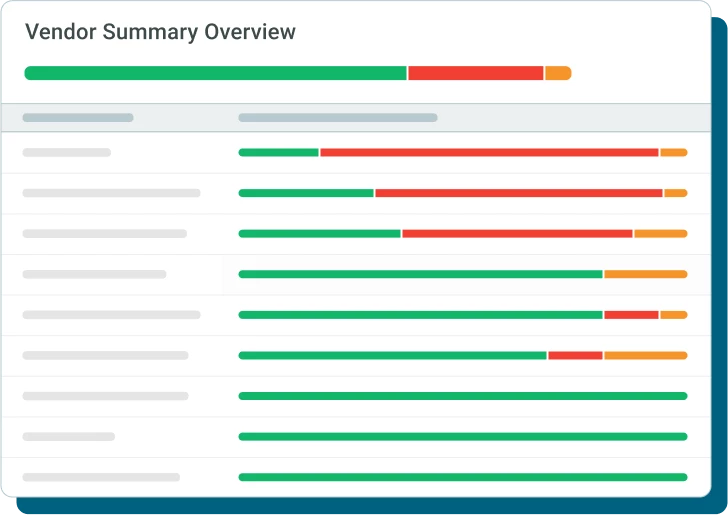
Vendor Summary
View the overall state of a third party’s security posture instantly without digging through mountains of security docs or waiting for a questionnaire response. AI Vendor Summary allows you to drill into vendor security details, view common risks using your preferred control framework, and generate reports that can be shared with stakeholders.
AI Leadership
“I have looked at ProcessUnity, Prevalent, Panorays, and Venminder. We have used MetricStream and Archer. I think the AI powered processing of TPRM that Whistic has engineered is a different class.
The traditional method of questionnaire administration, the cycle of back and forth between the vendor and the company has been completely done away with by simply reading through the documents with the AI tool. The resultant Vendor Summary is excellent. I have not seen anything like this and it makes me think that Whistic is definitely where no one else is.”
—Fortune 200 Financial Services Company
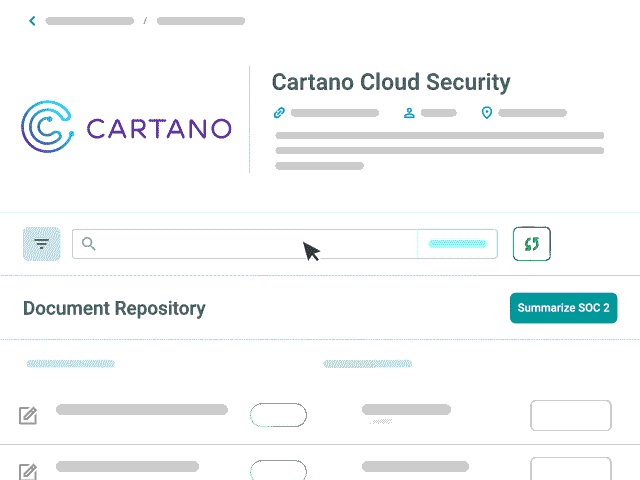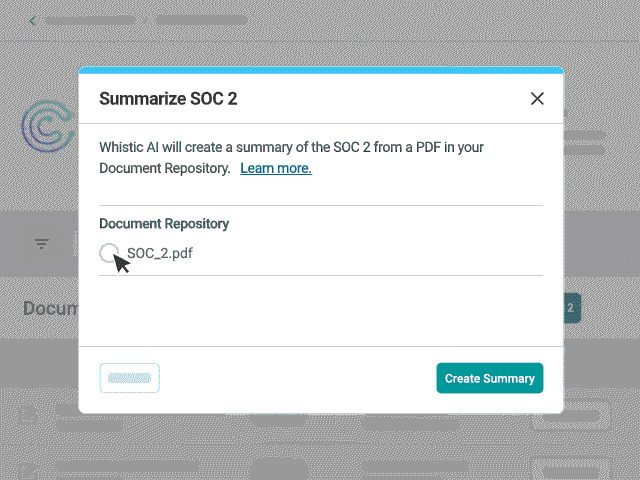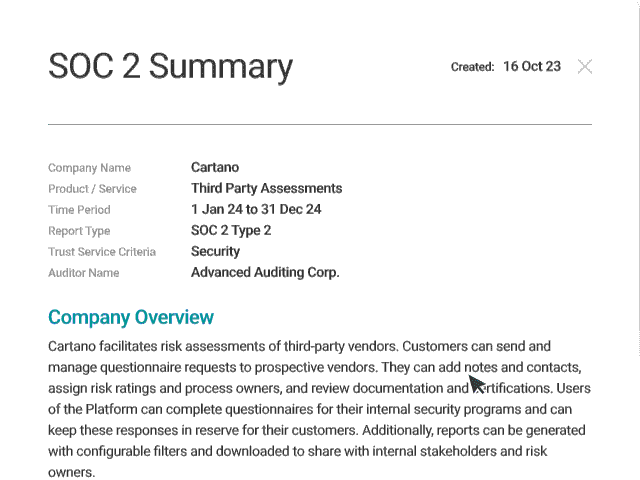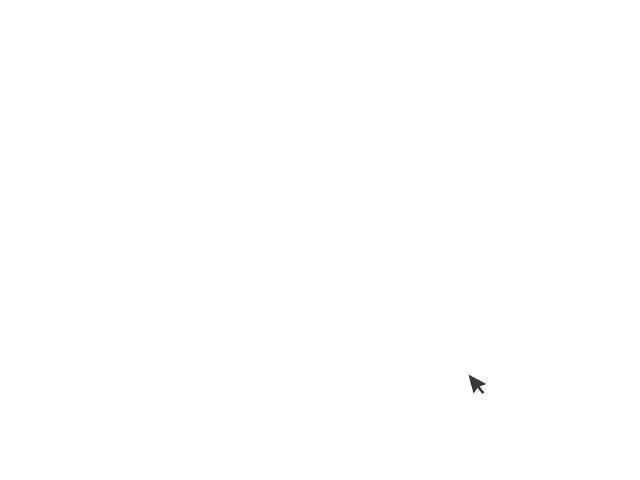
SOC 2 Summarization
Use Whistic AI to generate a summary of a SOC 2 audit report catered to your controls without manually searching through hundreds of pages of documentation — making it easier to gain important risk insights in a fraction of the time it typically takes.
Vendor Insights
Use Whistic AI to ask plain-text questions about vendors across all data sources and get definitive answers with links to the evidence in the source documents provided.
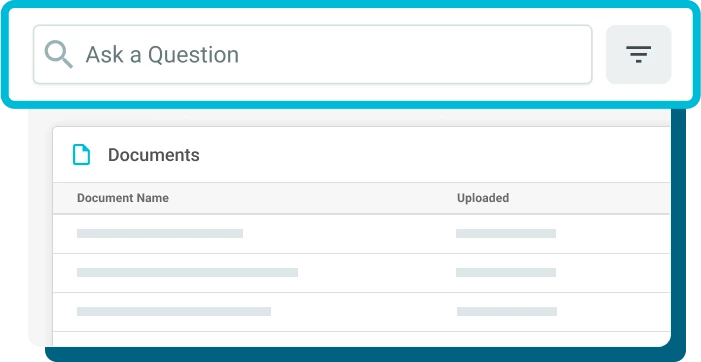
Knowledge Base with Smart Search
Organize all security and compliance documentation in a single repository and use Whistic AI to search it all with plain-text questions, getting definitive answers with links to the evidence in the source documents.

83% reduction in onboarding time
“Our time to assess went from 1 month (or often longer) to a point where 5 days is almost unheard of now. It’s usually less than 5 days and sometimes a couple hours to complete the assessment when they already have a Profile in place.”
—Largest University System in the U.S.


